- A crypto user lost nearly
$50 million in USDTafter copying a spoofed wallet address from transaction history.
- The attack used
address poisoning, exploiting wallet interfaces that hide the middle of addresses.
- Funds were quickly swapped and routed through multiple wallets, with portions sent to
Tornado Cash, limiting recovery options.
A single copy-paste mistake has resulted in one of the most expensive user errors ever recorded on-chain. The incident highlights how simple interface habits can override otherwise cautious behavior and lead to irreversible losses.
Table of Contents
How a Routine Test Transfer Turned Into a $50M Loss
According to on-chain investigators, including Lookonchain, the victim began with a step many experienced users consider best practice: a small test transaction. The user sent
That test transfer, however, became the trigger.
Within moments, a scammer deployed an address poisoning tactic. The attacker created a wallet address, which had the same first, and last four digits as the genuine address of the victim. A small transaction was then sent to the victim on this address which looked as the real one, making sure that it would be recorded in the wallet of the transaction history.
When the victim returned to complete the main transfer:
Address Poisoning: A Low-Tech Attack With High Impact
There is no need to hack personal keys or to make the use of smart contracts. It is dependent on human interface and behavior.
Why This Attack Still Works at Scale
Most wallets abbreviate addresses in order to enhance readability. Transfers are frequently checked by the user by checking the first and the last address. This is abused by attackers who generate addresses that reflect such visible characters.
In this instance, the scammer did this immediately after the test transaction and it signifies automatic monitoring. The attacker made convenience hide a better reason to take caution by placing a near-identical address in the history of transactions of the victim.
This method is considered basic compared with complex DeFi exploits. Yet the outcome shows that even “simple” scams can produce catastrophic losses when large sums are involved.
On-Chain Movements After the Theft
Blockchain records show that the stolen USDT did not remain idle. The attacker very swiftly exchanged the part of the funds to ETH and sent them to several wallets, which is typical to diminish the traceability.
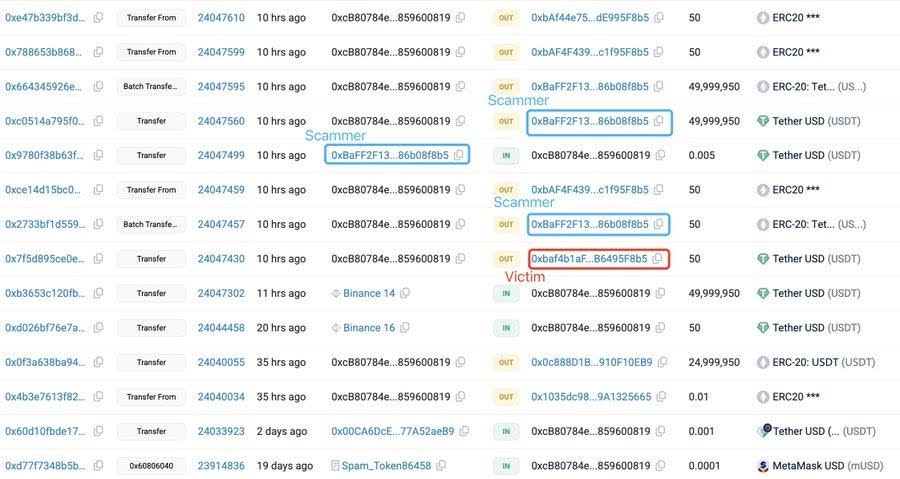
The assets were later transferred to Tornado Cash, a privacy mixer that hides the trails of transfers. As soon as the money is invested in such services, recovery is extremely unlikely without an immediate action of the exchanges or validators.
The chain of wallets was described by analysts who claimed it was efficient and preplanned meaning the scammer was all set to make an action as soon as the big transfer was made.
Why This Case Shocked Analysts
Address poisoning is widely known and often discussed as a nuisance scam involving small amounts. What makes this case stand out is the scale and the profile of the mistake.
The victim followed a common safety step by testing with a small transfer. Ironically, that action gave the attacker the signal needed to deploy the spoofed address at exactly the right moment.
On-chain observers noted that just seconds spent copying the address from the original source, rather than transaction history would have prevented the loss entirely. The speed of blockchain finality left no window for reversal.
Wallet Design and the Human Factor
This incident raises questions about wallet UX choices. Truncated addresses improve visual clarity but reduce security for users handling large sums.
Some wallets now warn users about address poisoning or flag addresses that closely resemble known ones. Others offer address whitelisting, where transfers are restricted to pre-approved addresses. Adoption of these features, however, remains inconsistent.
For high-value transfers, reliance on visual checks alone has proven insufficient. The case shows how even experienced users can fall into predictable patterns under time pressure.